Email security might not get your heart racing like a good thriller novel, but let’s face it: we’ve all been there. You’re about to send an email that should probably be sealed in a vault. Each time I hit ‘send,’ a tiny part of me holds my breath, worrying if my words are headed into the great abyss of the internet where they might get snatched up like a cookie on a diet. With more scams than a detective novel, knowing how to keep our messages safe is crucial. From encryption to understanding TLS, we’re going to break it all down. No need for a PhD in computer science here; just a sprinkle of curiosity and a dash of humor, and you’ve got it! So grab your coffee, and let’s explore the wild world of email security together.
Key Takeaways
- Understanding encryption is key to protecting your emails.
- TLS is vital for secure email delivery; it’s like a superhero cape for your messages.
- Common email vulnerabilities can skew your email experience.
- Anonymous SMTP services help keep your identity undercover.
- Adopting secure message pickup can make your email security efforts more effective.
Next, we are going to discuss how emails zip through the digital world like a chicken on a hot grill, all for the sake of communication. Spoiler alert: you’re not just tapping send; you’re orchestrating a surprisingly elaborate performance!
The Email Delivery Dance
How We Send Emails
Sending an email is somewhat like tossing a message in a bottle into the ocean. But instead of waves, we rely on techie stuff to carry our thoughts to far-off shores.
Imagine dropping your virtual letter into a mailbox marked “SMTP server,” which is essentially a high-tech post office.
When we’re sending that quirky joke or an important report, our email client—could be Gmail, Outlook, or even that dinosaur-like Apple Mail—talks to this newsworthy SMTP server.
It’s like having a chat with the mailman about where your message needs to go next, instead of just tossing a letter willy-nilly.
How Does the Delivery Work?
Once your email’s on the move, the SMTP server takes a gander at the recipient’s email address. If everything checks out and “Bob@Recipient.com” exists, the dance begins.
But if not? Well, think of it as a well-intentioned mailman trying to deliver a letter to a ghost. The server will leapfrog through other servers (backup ones) to ensure your email gets delivered.
If the recipient’s always “out to lunch,” then your email gets put on hold until it can find someone home to take delivery.
Finding the Right Path
Now you might wonder, how does the SMTP server even know where to send those emails? It’s all hidden in the DNS, which isn’t some fancy drink but a directory that reveals the servers available for the job.
If you’ve got multiple addresses, it’s like a game of musical chairs—there’s always a pecking order. The main server gets the first shot, while backup ones stand ready like loyal bodyguards, just in case.
It’s worth noting that an email might have a bumpy path, encountering various hiccups:
- Your server could successfully handover the email directly.
- A server could be overwhelmed, pushing your email to the first backup.
- Or, Chaos would reign and it could keep failing until it gives up, treating your email like a stubborn negotiator who won’t budge.
Opening the Email Vault
When the email arrives safe and sound, it sits securely in the recipient’s inbox, sort of like a secure vault at a bank.
To get to those sought-after messages, there are two main languages: IMAP or POP. Think of these as the secret codes that let you in to read your notes and cat memes sent by your friends.
Whether it’s through an email client or a web-based system, servers are always gabbing away, ensuring you get your daily dose of correspondence.
So, no matter if we’re toggling emails like a pro, there’s a surprising amount of behind-the-scenes orchestration happening in just a few seconds!
Next, we’re going to discuss why email security can sometimes feel like standing in a crowd with a megaphone, shouting your secrets. Trust me, it’s not as safe as it seems!
Email Vulnerabilities You Should Know
Email might just be the most convenient tool we’ve got for communication, but if we’re being honest, it’s a bit like leaving the doors of your house wide open while hosting a party. Let’s break it down:
- Web-Based Email: Imagine trying to send a postcard instead of a letter. If your email is sent through a plain ‘http://’ link, the only secret admirer getting your info is anyone snooping on the network! Passwords and personal messages float through the air like confetti at a parade, waiting to be snatched up.
- SMTP: Now, SMTP’s got a quirky rule—no encryption for messages unless everyone plays nice and supports SMTP TLS. So, if your email server asks for your login like a night bouncer, those details can be as visible as a neon sign. Eavesdroppers can watch your messages zip by, all while making a note of what device you’re using and possibly where you are!
- POP and IMAP: Logging into your email using these protocols can feel like handing out your house keys. Your login details flow back and forth as readable as a book, unless you’re on an SSL connection, which adds a tad bit of protection. Still, isn’t it a bit like putting a lock on your door after inviting the whole neighborhood over?
- Backup Woes: Picture this—your emails sitting in the server like snacks at a party. They’re easily accessible whenever backups are made, leaving your important conversations out there for anyone with the right access to munch on. You may think they’re gone, but they could be lurking around indefinitely!
Email security issues are everywhere, like those funny cat videos you can’t help but click on. In our next chat, we’ll explore the broader landscape of communication security. Spoiler: it’s as fascinating and alarming as an episode of your favorite drama series.
Now we’re going to explore some of the sneaky threats that lurk in your email communications. Think of it as a friendly chat about keeping your digital secrets safe, even when the internet feels like the Wild West.
Common Email Security Risks

Eavesdropping
Ever feel like someone’s listening in on your conversations? Well, it turns out they might just be! The internet is like an open book, and if someone’s got their ear to the ground (or rather, their wires connected), they could be reading your emails. It’s like someone in the next room picking up gossip through the wall, just less charming.
Identity Theft
Imagine if you woke up one day to find a stranger sending emails under your name, asking your pals for money! While it sounds like a plot twist from a bad sitcom, it can happen—in reality, if someone gets hold of your email credentials. They can nab these sensitive details through various sneaky means, from old-school eavesdropping to phishing scams. The dangers are as real as Aunt Edna’s fruitcake at Christmas!
Invasion of Privacy
Picture this: you send an email, and it accidentally reveals your secret location—like letting everyone know that your mom’s casserole recipe isn’t the only thing you’re hiding. Sensitive info like your IP address can provide potential snoops with a city, or worse, your exact address, so it’s essential to consider how secure your backups are.
Message Modification
Have you ever had a friend embellish a story (you know, the one about the fish that got away)? Emails can suffer a similar fate! Anyone with access to the SMTP servers can fiddle with your messages. They could change the content, and the recipient would be none the wiser. Talk about a digital game of ‘telephone’!
False Messages
With some creativity, crafting messages that look like they came from your favorite celebrity is a piece of cake. Bad actors can fool your family into thinking they’re receiving emails from you. Just like a magician pulling a rabbit out of a hat, it’s easy to create an illusion that can spread malware or misinformation.
Message Replay
Ever get a sense of déjà vu? Imagine receiving a message you thought had already been dealt with! That could mean someone saved your original email and sent it out again… faked and all! Automated systems that act on email contents can really take a hit from this one.
Unprotected Backups
Emails stored like dusty letters in an attic? Yes, please! But sometimes, backups are just plain text laying around servers, waiting to be discovered by anyone with access. Even if you think you’ve deleted them, they’re sneaky—they can linger like last week’s leftovers.
Repudiation
We’ve all seen those courtroom dramas where someone denies sending a message. It can happen in real life, too! Since email isn’t exactly a Fort Knox of security, proving someone sent a particular email is like finding a needle in a haystack. This causes headaches for businesses that rely on emails for contracts and important communications.
| Threat Type | Description |
|---|---|
| Eavesdropping | Unauthorized interception of emails |
| Identity Theft | Using someone’s credentials to send false messages |
| Invasion of Privacy | Revealing personal information like IP addresses |
| Message Modification | Changing content without the sender’s knowledge |
| False Messages | Sending emails that appear to be from someone else |
| Message Replay | Re-sending previously sent messages with modifications |
| Unprotected Backups | Emails stored insecurely on servers |
| Repudiation | Denial of sending a specific email |
Now we are going to explore the essentials of encryption, a topic that’s crucial for keeping our online communications safe. Grab a coffee because it’s time to break down the nitty-gritty of symmetric and asymmetric encryption—and maybe share a laugh or two along the way!
Understanding Encryption Types
Symmetric Encryption
Imagine you and a buddy are passing secret notes in class, using a code only you two understand. That’s pretty much how symmetric encryption works! You slap a “secret” key onto your message, and voilà, it turns into a jumbled mess that only your friend can decode—if they’ve got the same key, of course.
It’s like exchanging secret handshakes—handy, right? Without the key, that cyphertext looks like gibberish. This method keeps prying eyes at bay.
But here’s where it gets tricky: sharing that secret key. If you’re sending messages across the globe, how can you ensure that no sneaky eavesdroppers are listening in? You wouldn’t want to send it along with your Wi-Fi password! So yeah, while symmetric encryption does a great job shielding our messages, the key-sharing process can feel like trying to get a cat into a bathtub.
Message Digests and Authentication Codes
Now, let’s talk about Message Digests or Message Authentication Codes. Think of these as tiny fingerprints for your messages. They’re created by running your message through a special algorithm, resulting in a shortened version that’s nearly impossible to reverse-engineer.
When you send a message, it’s like sending a digital selfie with a watermark—keep track of those fingerprints when comparing. If you receive one without deviations, well, it’s all good! It’s almost like allowing your best friend to borrow your favorite sweater but checking that it comes back without mysterious stains.
Asymmetric Encryption
Now we flip things on their head with asymmetric encryption. This is a bit like having two keys: one is public, and the other is private. When your colleague sends you a message using your public key, only your private key can unlock it.
No need to share this key in a group chat—thankfully! This method gives us all sorts of exciting abilities, like:
- Send Encrypted Messages: Securely send a message with the recipient’s public key. Only they can open it. It’s like a surprise party—you don’t want anyone spoiling the surprise!
- Prove You Sent a Message: Simply encrypting with your private key allows anyone with the public key to verify that you sent it. It’s like signing a postcard from vacation—proof you were indeed sipping piña coladas on the beach!
- Sign Messages: Add a signature to your message for authenticity. Think of it as a guarantee that you’re the chef behind that gourmet meal (or, in this case, the message).
- Send Encrypted, Signed Messages: Combine it all for the ultimate communication armor. It’s like wearing a lock and carrying a spare key just in case. Does it get tougher than this? I think not!
And there you have it! Encrypting our digital smoke signals doesn’t need to be a headache. So, next time you send a message, consider the magical world of encryption to keep those private thoughts safe from wandering eyes!
Now we are going to talk about how to keep our emails safe, using TLS. This not-so-secret ingredient is like the invisible superhero of email security.
Email Security with TLS: What You Need to Know
So, if you’re like us and sometimes feel like a techie superhero (or at least you pretend to be), then you’ve probably heard of Transport Layer Security (TLS). This clever little system makes sure we’re not just chatting into the void or worse, to an imposter hiding behind a computer screen.
Using TLS is as simple as pie, and let’s be real, who doesn’t love pie? When we connect to a server through TLS, it’s like shaking hands with the right person at a wrong-party. Here’s the breakdown:
- The server flashes its private key, proving it’s legit.
- We send the server our public key, like saying, “Here’s my ID!”
- The server crafts up a secret key and sends it over to us — all wrapped up in our public key for safety.
- Finally, we chat away using this secret key that keeps our conversation fast and secure.
The beauty of TLS? It ensures that:
- We’re chatting with the right server.
- Our conversation remains a secret. No peeking!
If we see any warning signs while using TLS, it’s like receiving a smoke signal that something’s off. Sure, our email provider might just have a small hiccup, but let’s not ignore a potential digital mugger trying to listen in on our gossip sessions!
Those warnings could mean:
- Uh-oh, the server’s SSL certificate has gotten old and cranky.
- The details in the certificate don’t match up with what we expected – like showing up to the wrong restaurant for brunch (we’ve all been there).
- An untrusted agency issued the certificate – might as well be that friend with dubious taste in movies!
- Someone’s eavesdropping, like that one person at the party who stands too close.
Certificates are typically handed out by third-party agencies. They do some homework before approving a company’s request. So, when we see that a certificate is valid, it adds a bit of sunshine to our email days. It confirms we’re where we intended to be.
Using TLS ensures our messages, logins, and even our cat memes stay hidden from nosy observers, at least until they hit the SMTP servers. It’s like making sure our secrets are safe during transit – but let’s not forget, they might not stay that way forever once they reach their destination.
Implementing TLS is easy-peasy; a few clicks on our email client, and voilà! It’s like putting on a seatbelt before a road trip. Let’s remember, TLS protects us better than anything else – we should definitely think twice before forgoing it.
So, in the grand adventure of email, let’s keep it secure. After all, who wants to survive email drama when we can zip past it with TLS? Cheers to safe emailing, friends!
Now we are going to talk about how we can keep our emails private, even in a digital world that seems to share everything. Spoiler alert: it’s not as scary as it sounds! Let’s explore some intriguing tools that help us retain some of our precious privacy while still being able to send emails without a hitch.
Email Privacy with Anonymous SMTP Services
You know that moment when you send an email, and suddenly, you feel exposed, like a cat in a room full of rocking chairs?
Well, when we send emails through most email clients (WebMail is a bit of an exception), our computer’s IP address tags along for the ride. Yup, that little piece of information can expose where you are faster than a speeding squirrel!
As we seek to protect our privacy, it’s crucial to understand how this little detail can matter.
Now, for folks who are a bit paranoid about their online footprint (and rightly so!), anonymous SMTP services come to the rescue, acting like the digital bouncers we never knew we needed.
These services work by receiving your email through their servers and performing a bit of a magic trick with it: they scrub away any identifiable information. Think of them as the ultimate email sanitizers, ensuring that when your message reaches its destination, it’s clean, clear, and anonymously you.
Recipients get your email without the ability to trace it back to where it originated. They can see who you are through your email address and the content you’ve sent, but anything revealing your whereabouts or the email program you used? Poof! It’s all gone!
But wait, there’s a catch. Most of these services do keep an eye on the information they’ve scrubbed from your messages. It’s like that friend who you told a secret to, and now they’re keeping tabs on it. Your email service provider may know where you are, though the recipient doesn’t. This is particularly useful when dealing with unsolicited or shady emails. Your provider can swiftly handle any trouble. No one wants to be on the wrong end of legal trouble, right?
The level of privacy offered here is akin to sending emails through a WebMail interface. So, if you’ve been feeling like a fish out of water, anonymous SMTP can be your saving grace!
For those using LuxSci, they provide these services to clients with SMTP relaying features. All we need to do is tweak a port here or there (easy peasy!) to benefit from their robust system.
Using an anonymous SMTP service can lighten the mental load, giving us a bit of peace of mind as we navigate our inboxes without leaving a digital footprint. We all deserve a little privacy in our lives!
So, as they say, “A little preparation goes a long way.” Why not gear up with anonymous SMTP and keep that pesky IP address under wraps?
Now we are going to talk about how to make our emails more secure. You know, those pesky little messages that have pets-barking-level secrets? We’re diving into email security, specifically through asymmetric key encryption like PGP and S/MIME. Let’s aim to batten down those hatches and keep those prying eyes away from our inboxes!
Email Protection Through Asymmetric Encryption Techniques
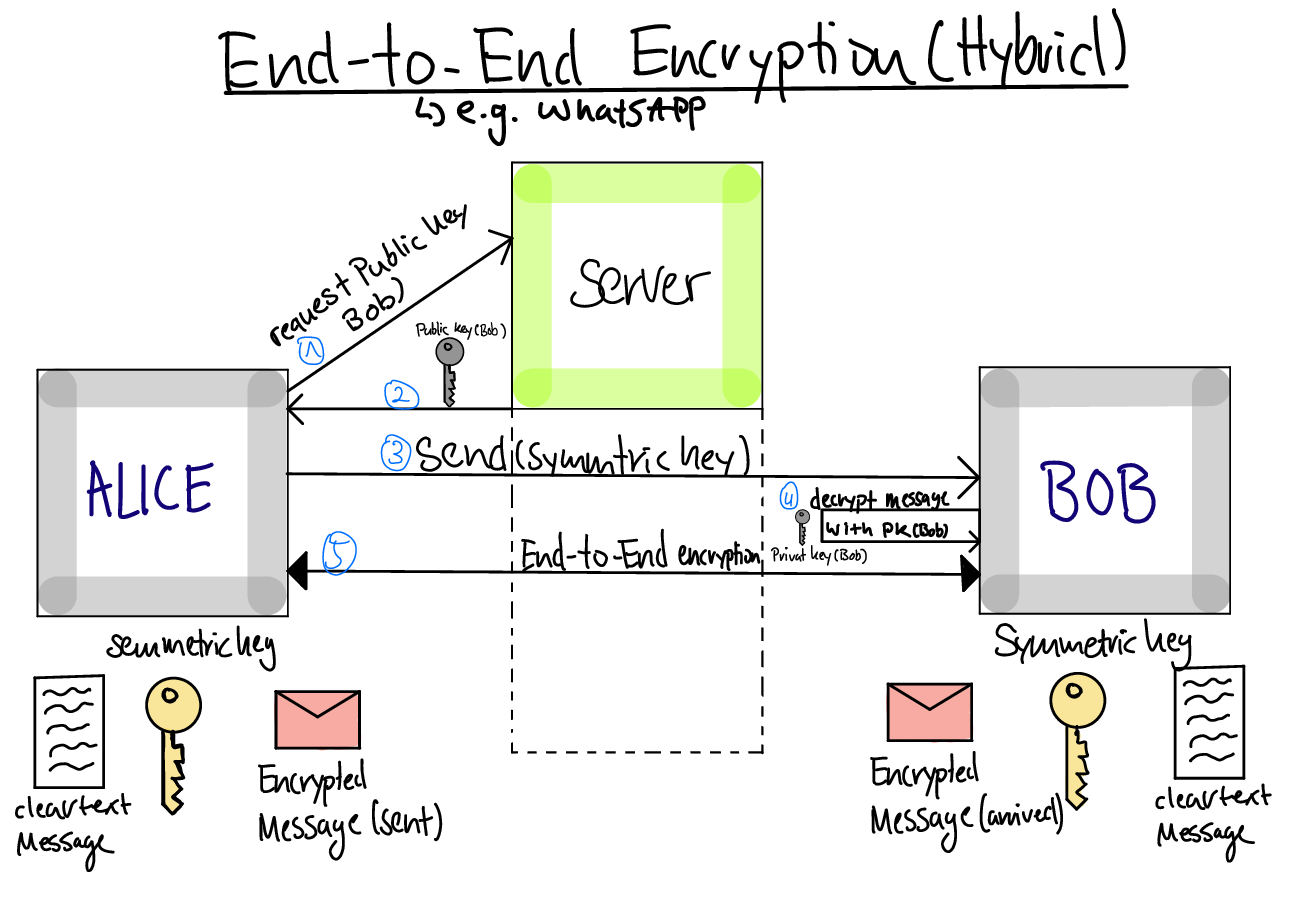
TLS, or Transport Layer Security, is like that lukewarm cup of coffee that does its job in the short term but is no match for the big issues at hand. It keeps your password safe while you’re sending emails, but once those emails are stored or hopping servers that don’t support TLS, it’s like leaving your front door wide open with a neon sign saying “Come on in!”
The real heros in the email world are asymmetric key encryption solutions like PGP and S/MIME. They’re like those super friends in capes who swoop in to save the day, tackling:
- Eavesdropping (because everyone hates being listened to)
- Message modification (no one likes a message that changes its story)
- Message replay (nobody wants to relive bad moments)
- Repudiation (proof of sender = no finger-pointing)
- Unprotected backups (keeping all your secrets where they belong)
When you pair asymmetric encryption with SSL, you’re ensuring that even your most mundane email details, like usernames and subject lines, are fully protected. Remember, it’s the little things that count—those things aren’t in the body of your message but they’re still prime targets!
So here’s the scoop on PGP and S/MIME: both are commonly used, but they have their quirks. Serious email users who want to be secure need to think about which one to use. PGP is like the hipster coffee shop of email encryption—everyone knows it, and it’s been around since 1997, but you might have to go out of your way to make it work. S/MIME, on the other hand, is your friendly neighborhood coffee chain—readily accessible but requires a membership card.
Crossover Challenges
While PGP and S/MIME throw punches at email security problems, they also create their own set of challenges—chiefly, interoperability. It’s akin to dating: if you’re using one app and your date is on another, good luck connecting!
PGP offers a foundation thanks to its OpenPGP standard, but don’t get too cozy. If your buddy prefers S/MIME, the email equivalent of two ships passing in the night is in your future. Yes, S/MIME tends to be more user-friendly as it lives in many email clients, but, oh boy, the certificate management can get tedious. And some clients, like Microsoft Outlook, have the fascinating ability to juggle both options! Who says email can’t be entertaining?
And then there’s the key exchange. Before you can send that encryption party invitation (also known as an email), both parties need to swap public keys. It’s like sending out invitations for a secret meeting but not telling anyone where the party is. PGP’s key servers can simplify this, but it’s not a sure bet since not everyone’s playing along. And if you need speed? Well, let’s be real, the struggle is real!
| Issue | Solution with PGP | Solution with S/MIME |
|---|---|---|
| Eavesdropping | Always encrypted | Always encrypted |
| Message modification | Message digests | Message digests |
| Message replay | Timestamps | Timestamps |
| Repudiation | Signature proof | Signature proof |
| Unprotected backups | Always encrypted | Always encrypted |
Keeps those keys close, and let’s secure those messages! It’s all fun and games until someone loses an email! So, let’s stay smart, keep those communications tight, and remember to have a little fun while we’re at it!
Now we are going to talk about ways to boost email security in a friendly, relatable manner. It’s a topic we can all nod along to, especially if you’ve ever faced the dreaded moment of hitting “send” and wondering if your precious message will safely reach its destination. So, let’s jump right into how email security can become a smooth ride.
Email Security That Works for Everyone: Let’s Get to Know “Secure Message Pickup”
Imagine you’re trying to send a top-secret recipe for Grandma’s famous chocolate chip cookies. But instead of just emailing it, you decide your kitchen wizardry deserves extra security. That’s where Secure Message Pickup comes in. It’s like having a trusty middleman who ensures your recipe doesn’t fall into the wrong hands.
Let’s break down how this works:
- The sender connects with our helpful middleman via a secure TLS connection. It’s like stopping by a trusted neighbor’s house to drop off something special.
- Our middleman does a little background check on the sender. “You’re good to go!”
- Next up, the sender crafts the message. Yes, even a recipe can be well-articulated.
- Then, the sender picks a secret handshake – maybe a password or a riddle – to verify the recipient’s identity.
- The middleman takes the message, gives it a good encryption scrub (think secret agent level), and tucks it safely away.
- Now, here’s the clever part. The middleman sends a casual email to the recipient with a link to access their message and a unique password. Once that’s done, the middleman forgets the password, so only the recipient can unveil the message!
- When the recipient clicks the link, voila! They log in over a secure connection.
- The middleman decrypts the message and reveals it to the recipient. Time to share that cookie recipe!
This system tackles security concerns, and here’s how:
- Eavesdropping: Thanks to that secure TLS connection, snoopers can’t overhear anything. It’s like gossiping behind a locked door.
- Identity Theft: Since both parties use TLS connections, it’s tougher for peeping toms to steal login details. A win for privacy!
- Invasion of Privacy: Recipients won’t know the sender’s business. Just that they used “the middleman.” Like a mystery pen pal!
- Message Modification: The message is locked away on the middleman’s server, so nobody can change it. It stays true, like a loyal friend.
- False Messages: Thanks to the secure nature, only the intended audience sees it. No impersonators here!
- Message Replay: No sending it again without the middleman’s say-so! It’s like “one and done.”
- Unprotected Backups: Even backups of the message are secure because it stays encrypted.
- Repudiation: The middleman validates that the right person sent it, so there’s no denying it.
Let’s face it; email security can feel like a roller coaster – thrilling but nerve-wracking. With services like this, we can all worry just a bit less and laugh a bit more, knowing our secrets, well, stay secret! So, let’s give a little nod to swift communication without sacrificing safety. Here’s to sending messages with confidence!
Just a word of advice, though: if you’re not the middleman’s biggest fan, always ensure they’ve got a good reputation. As with any relationship, trust is key!
Now we are going to talk about how email security has a new flair with SMTP TLS, a subject that keeps getting more interesting!
Email Security: The TLS Twist
It’s amusing how email security can sometimes feel like a game of musical chairs.
With SMTP servers now embracing something called “opportunistic TLS,” we see a shift in how our messages make their way from point A to point B. Imagine two servers shaking hands and agreeing to wear their protective gear—you feel good knowing your email is zipping through the digital ether safely. But, hold onto your hats!
- Not all email providers are on board with this TLS party yet. It’s like showing up to a potluck and realizing someone forgot the lasagna.
- If your favorite server is still rocking outdated security, you might as well be tossing your emails into a pool without a lifebuoy.
Enter LuxSci with their take on security: “Forced TLS.” What is that, you ask? Well, buckle up!
If you send an email to someone whose server plays nice with TLS, it’ll either be delivered securely or sit in limbo until everything aligns perfectly.
It’s like waiting for that signal from your Wi-Fi to finally connect—frustrating, yet satisfying when it works!
- Emails headed to recipients with TLS support will either jump through the TLS hoops or not get delivered until the stars align.
- For those stuck with servers not yet on the TLS train, fear not—email will gracefully “fallback” to alternative encryption methods, like Secure Message Pickup. It’s like getting a plan B when the restaurant runs out of your favorite dish!
Now, if you find TLS is the best fit for your needs, that’s fantastic!
It’s practically hassle-free, allowing you to keep the wheels of your business turning without dropping the ball on security.
We all know that smooth sailing makes life easier; just keep it strong with those who support it and adapt with a backup plan for everyone else. After all, who wants to deal with email drama? Let’s stick with what works!
Now we are going to talk about why email security is more important than ever, along with some smart ways to lock things down. Let’s face it, if we had a dollar for every time someone got hacked through email, we could probably fund a small island getaway. But before we start daydreaming about palm trees, let’s get into the nitty-gritty.
Why Secure Email Matters

Email is like that old diary we used to have—full of secrets and intimate thoughts, just waiting for someone to peek inside. Yet, unlike a diary, we often don’t pay attention to who’s reading our emails. Recent news about data breaches showcases how fragile our email can be, with hackers sniffing around like they’re looking for the last slice of cake at a party.
We ought to be mindful of the major threats to email security:
- Eavesdropping
- Identity Theft
- Privacy Violations
- Message Tampering
- Spam and Phishing Scams
- Message Resending
- Unsecured Backups
- Disputed Emails
How to Enhance Your Email Security
TLS: Think of TLS (Transport Layer Security) as a bouncer at a nightclub, ensuring that only authorized folks get in. It’s pretty straightforward to implement, securing the lines between our computers and the email service provider. Here’s what TLS accomplishes:
- Ensures we’re connecting to our service provider—not some shady operator.
- Encrypts our login info to prevent sticky fingers from stealing our credentials.
- Shields our messages from prying eyes while in transit.
Anonymity: Who doesn’t love a bit of mystery? If we can use an Anonymous SMTP server, our web presence becomes as elusive as a cat avoiding a bath. This set-up offers:
- Privacy for our IP address, so recipients can’t track where we are.
- Discretion over our email clients, keeping nosy people guessing.
- A chance to scrub any unwanted header data that tags along with our messages.
PGP and S/MIME: These two old pals use asymmetrical encryption to safeguard our messages from the moment we send them out until they reach their destination. They help with:
- Guarding against eavesdroppers and rogue backups.
- Creating message digests to verify if anything went awry while traveling.
- Signing our messages to prove authenticity, like a digital signature on a check.
Now, while we strongly recommend using TLS, it’s sad that PGP and S/MIME aren’t more popular. Setting them up is like trying to teach a cat to fetch—difficult and often unsuccessful. Yet, as we see more companies leaning into secure messaging, the tide is turning.
Secure Message Pickup is a user-friendly option that sidesteps many complications of traditional encryption. It lets us communicate safely without needing an instruction manual the size of a textbook. Imagine sending secure emails as casually as posting on social media.
Forced TLS is great if we want consistent encryption without being on high alert, but let’s be real: email security problems can be stealthy. They usually sneak in unnoticed until it’s too late, leaving us scratching our heads while wondering what went wrong.
If there’s any lingering confusion about email security, don’t hesitate to chat with experts. Just remember, it’s not about being paranoid—it’s about being prepared!
| Security Threats | Protection Methods |
|---|---|
| Eavesdropping | TLS, Anonymity |
| Identity Theft | TLS |
| Privacy Violations | Anonymity |
| Message Tampering | PGP, S/MIME |
| Spam and Phishing | TLS, Awareness |
| Message Resending | PGP, S/MIME |
| Unsecured Backups | TLS, Secure Message Pickup |
| Disputed Emails | PGP, S/MIME |
Conclusion
As we wrap up our chat about email security, remember: it’s all about knowing what you’re dealing with. With all the cyber chaos out there, a little knowledge goes a long way. Protecting your email isn’t just a techie concern—it’s a personal investment in your privacy. Whether you’re using TLS or an anonymous SMTP service, staying informed keeps you a step ahead. So don’t just send and forget; pay attention to how you manage your email. Stay savvy, stay safe, and keep those inbox gremlins at bay!
FAQ
-
How does sending an email work?
Sending an email involves using an SMTP server, which functions like a high-tech post office to route your message to the correct recipient. -
What happens if the recipient’s email address doesn’t exist?
If the email address is invalid, the SMTP server will try to deliver it through backup servers or put the message on hold until it can find a valid delivery point. -
What role does DNS play in email delivery?
DNS acts as a directory that reveals the appropriate email servers for routing messages to the intended recipients. -
What are the main protocols for retrieving emails?
The main protocols for accessing emails are IMAP and POP, which allow users to read messages stored securely in their inbox. -
What are some common email vulnerabilities?
Common vulnerabilities include eavesdropping, identity theft, invasion of privacy, message modification, and unsecured backups. -
What is symmetric encryption?
Symmetric encryption involves using the same secret key for both encrypting and decrypting a message, which can complicate key sharing. -
What is the purpose of TLS in email security?
TLS (Transport Layer Security) is used to encrypt the connection between email clients and servers, ensuring that messages remain private and secure during transit. -
How do anonymous SMTP services help protect privacy?
Anonymous SMTP services anonymize the sender’s IP address, keeping the sender’s location and identity hidden from recipients. -
What are PGP and S/MIME used for?
PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions) are encryption protocols that protect email messages from eavesdropping and tampering. -
What is Secure Message Pickup?
Secure Message Pickup is a method that allows a sender to securely share a message through a middleman service that encrypts the message and verifies the recipient’s identity, ensuring secure communication.